So, you've started your journey to the cloud, experienced the power of identity and access management and are successfully protecting your infrastructure against mean little monsters? Then it's time to tackle your security management!
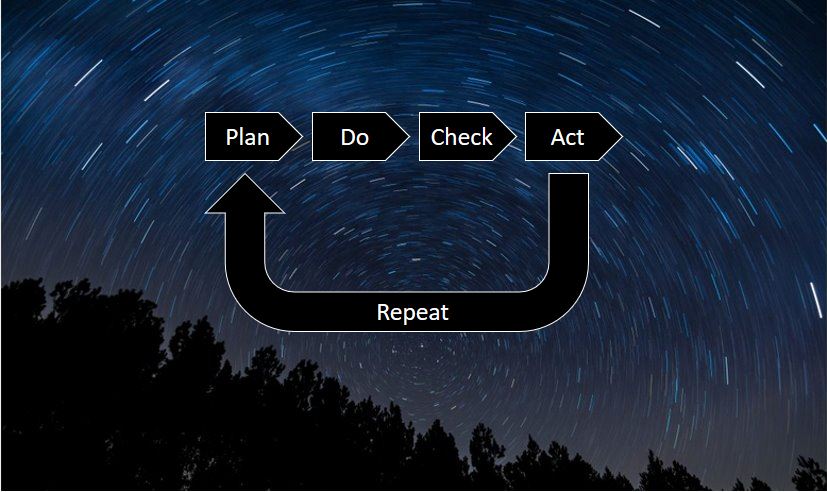
Security Management ensures that security levels are continuously maintained, visibility created, and new resources brought into line. From a process perspective, we have the methodology of a PDCA lifecycle. PDCA describes a control circle formed by four steps: Plan, Do, Check and Act.
This control circle is iterated for performing the activities of the individual phases:
- Plan: A goal is formulated, assumptions are made and key indicators are defined. These parameters result in measures (e.g., safety guidelines/safety goals)
- Do: The plan is implemented, but not all measures are mandatory (e.g., safety concept, implementation of technologies)
- Check: It is checked which effects occurred during implementation of the plan and whether measures need to be modified (e.g., implementation control, operational monitoring)
- Act: Final implementation of the measures (optimization, improvements)
Source: Negative Space/Own
Rerunning these phases ensures that the security level will be maintained. This methodology is very effective but can very quickly generate labor and tie up capacity. This is where the primary tool for security management in Azure comes in.
Join me in establishing contact and accompany me on an adventure, involving time travel, futile resistance and assimilation:
First contact (Plan/Do)
„I am the beginning, the end, the one who is many. I am the Borg.!“
– Borg Queen

Source: Sketchfab
Just like the Borg Queen, the Azure Security Center lies at the tip of the collective consciousness of security management in Azure. Policies, logs and Log Analytics Workspaces, security controls and vulnerability management all form part of this collective.
As a default, the "free tier" is active (Azure Defender off), so that only basic functionalities are available. For this reason, it's necessary to activate the Azure Defender, select the resources to be monitored, and then the Queen the security center begins its work and brings us closer to our goal.
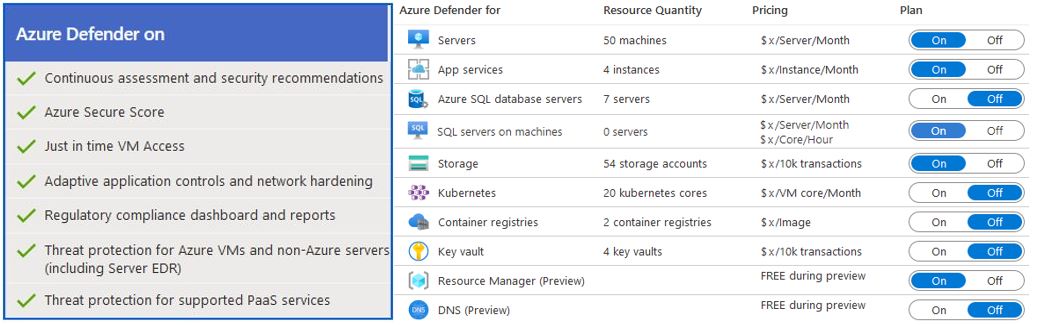
Source: own representation
After activation we inform our collective of the contact to be established in case of alarms.
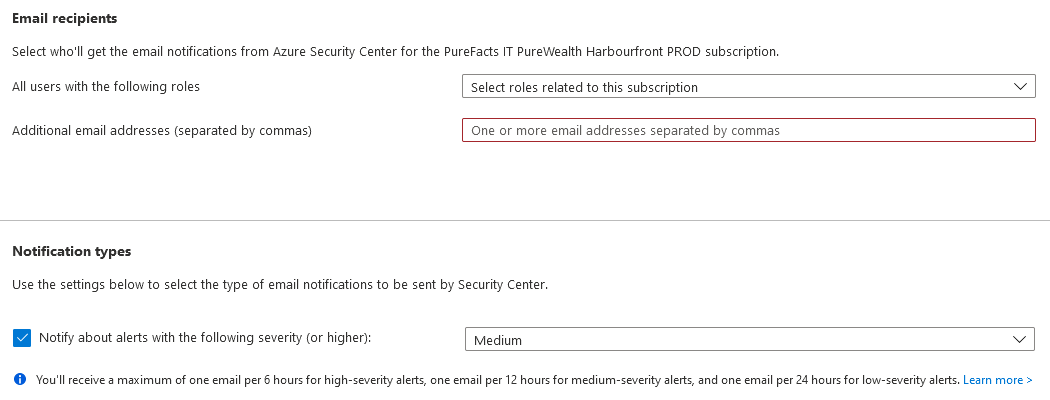
Source: own representation
After successful initiation, the full power of the security management lies at the collective's disposal, and we can begin the next phase!
Assimilate! (Check)
Now is the time to use the power of our collective to get an overview. Here the Azure Security Center, with its recommendations, built-in policies and other technologies, provides the required tools for the comprehensive implementation of security management.
First we'll dedicate ourselves to the task of bringing the available resources into line and, by use of our drones agents, generating a view.
Our Queen acquires her information via the Log Analytics Agent, the Microsoft Dependency Agent, and the expansion for vulnerability management. These agents can be distributed manually through the recommendations of the Azure Security Center, or provisioned automatically. Since we, as a collectively acting swarm, want to ensure that no entity slips our sight, we utilize the automatic distribution and assimilation of resources.
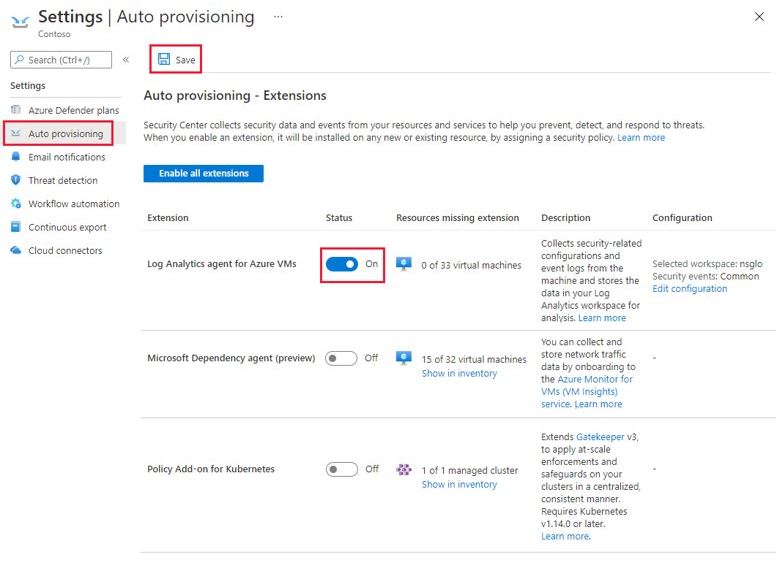
Source: Microsoft
Once "auto provisioning" is activated, our drones swarm out and all matching resources become assimilated! This applies to both existing and future resources.
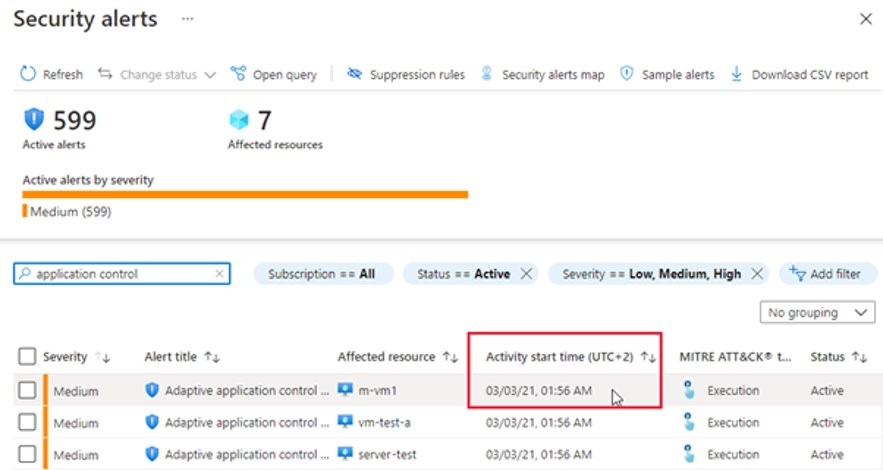
Now that we've come closer to our ultimate goal of a uniform configuration, we can look at how to proceed in identifying any defective drones. We detect drones resources that are vulnerable or behaving unusually by means of “adaptive application control” and by scanning for weaknesses.
The "adaptive application control" is a technology controlled by our collective and recognizes what is running on the drones. It detects malware, obsolete applications, prevents the execution of unwanted applications and generates a view of the data that is accessed by applications.
After activation of the "adaptive application control" it is necessary to configure the set of rules. This allows that all activities not complying with the operational standards of our drones will be signaled by an alarm.
Source: Microsoft
Now that we have the ability to look for deviants within our collective, it's time to identify potentially vulnerable entities and bring them to a non-vulnerable state.
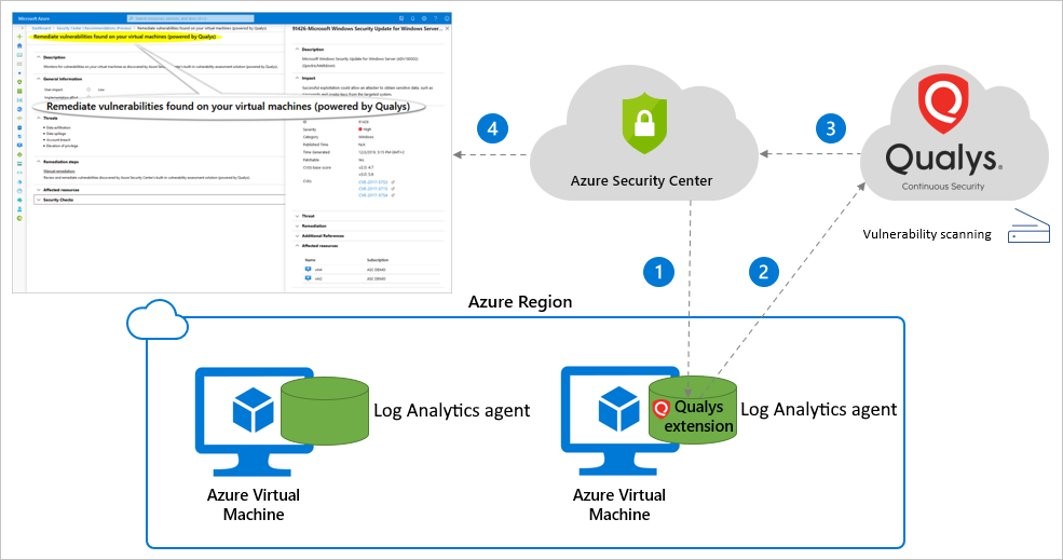
To protect our drones against attacks from outside or within the collective, we focus on the standard technology of our Queen the Azure Security Center. This is where Qualys comes in. Qualys scans our drones to detect any vulnerable configurations or weak points of a different kind.
Source: Microsoft
To this end, the corresponding extension is distributed among our drones. The extension scans the resource, aligns itself with the Qualys server, and reports the results to the Azure Security Center. On detecting findings of the middle to critical category, our Queen triggers an alarm.
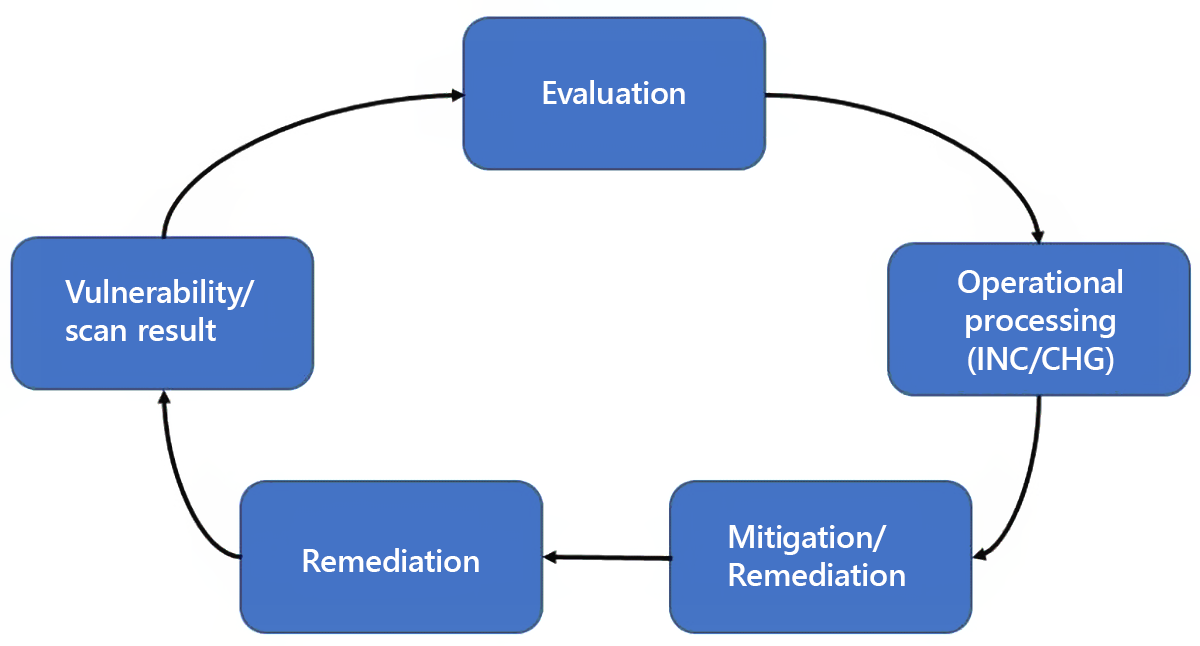
The weak point management of our collective must also undergo a process, so as to close the identified weak points and remove the vulnerability of our drones.
We therefore recommend implementing a regularly run process.
Source: own representation
By taking these measures and integrating the underlying process we have generated a certain visibility and are protecting our collective from attacks! We next turn to best practices for maintaining this security level and continuously improving the collective.
Resistance is futile! (Act)
It's futile to evade the growing demands on cyber security and the increasing threat situation. The question is not if your collective will be attacked, but when. And it's indispensable to support the technical solutions with strong processes in the context of security management.
Hence my recommendations:
- Implement sustainable process lifecycles
- Rely on a central, technological solution for mapping the security management
- Create the visibility you need
- Include the responsible employees in the collective
Today we established the initial contact and ran through different phases of the security management with our Queen. We laid the foundation for comprehensive security management in Azure. But note that the processes and technologies set up so far form only one part of the measures required to protect your collective!
Combine the measures of security management with those carried out previously, eradicate the individuality and vulnerability of single entities from your collective and ensure the inviolability of your resources! We are the Borg!
Author: Dominic Iselt, IT Security Engineering Expert
